Part 9 – Reverse engineering android applications

Welcome to the part 9 of lazy android developers series and here you go with the very first article of the 2015. So far we have talked about android libraries and development tools using which any android developers could save their valuable time, could reduce boilerplate code, could maintain coding standards, prepare wireframe/mockup design and save valuable time of making run-time changes. Today we are going to talk about reverse engineering android applications which would be fun!
Some of the parts of this series:
- Part 5: We talked about asynchronous image loading libraries, we did comparison of some libraries too, like Picasso, volley, Universal Image loader.
- Part 6: We talked about Staggered GridView which is ultimately a GridView having multiple columns with rows of varying sizes.
- Part 7: We talked about Useful tools for the android application development like Postman, JSONViewer, TinyPNG and many others.
- Part 8: We talked about wireframe design, mockup/prototyping android application.
In this part
Today, we are going to discuss about the importance of reverse engineering and procedure to do it. Reverse engineering android applications can help in many ways, either it be to get designs/layouts or piece of code from the applications. Hope you get why I am writing this part under lazy android developer series 🙂
Brief about reverse engineering
Reverse engineering is nothing but a process to extract knowledge or useful information from any product, whether it’s applied while rebuilding a bike or a car or any human made product. [Reference: Wikipedia] You would come to learn many new and interesting stuffs after breaking down the actual product into the different parts and putting them together again.
Originally this concept was originally applied to hardware only but now it’s also being highly used in software, to enhance the existing software or to duplicate it. The aim behind applying this process into software is software gets developed using programming language (which can be understandable by any programmer) which gets compiled using compilers and creates binary code (i.e. machine language, which can be understandable by system), so reverse engineering process comes into the picture when this machine language code requires to be converted back into the readable code using decompilers.
Anatomy of an android app
It’s a format used to package and distribute android application. An APK file contains all of that program’s code (such as .dex files), resources, assets, certificates, and manifest file.
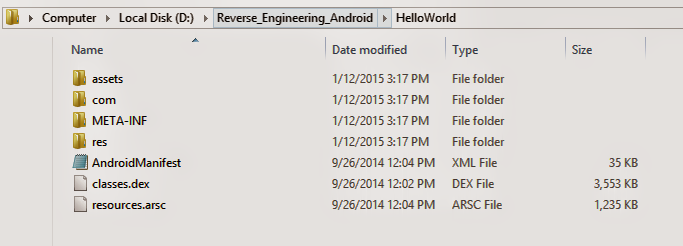
Interesting thing is, It’s just an archive file renamed with APK extension. To check, just rename it with zip extension and extract it, you would get below resources:
Tools – Reverse engineering apk
Below are some of the tools which I have been using to perform reverse engineering. If you know any good tool then please share it in comment, will definitely check and explore those it!
- Dex2jar
- Java decompiler
- Apktool
- Apk Analyser
Dex2jar
Download Dex2jar
Android programs are compiled into .dex (Dalvik Executable) files, which are in turn zipped into a single .apk file on the device. dex files can be created by automatically translating compiled applications written in the Java programming language.
Having said that, APK contains .dex file, to check that just rename the .apk file with .zip file and you would get classes.dex file. Just for the more information, dex is dalvik executable and it is actually a compiled code file.
As name itself is self explanatory, the main purpose of Dex2jar tool is converting DEX (dalvik bytecode) to JAR (Java bytecode). It also provides a capability to modify .class files in jar and build again the jar and translate it back to dex.
Java decompiler
Download JD-GUI
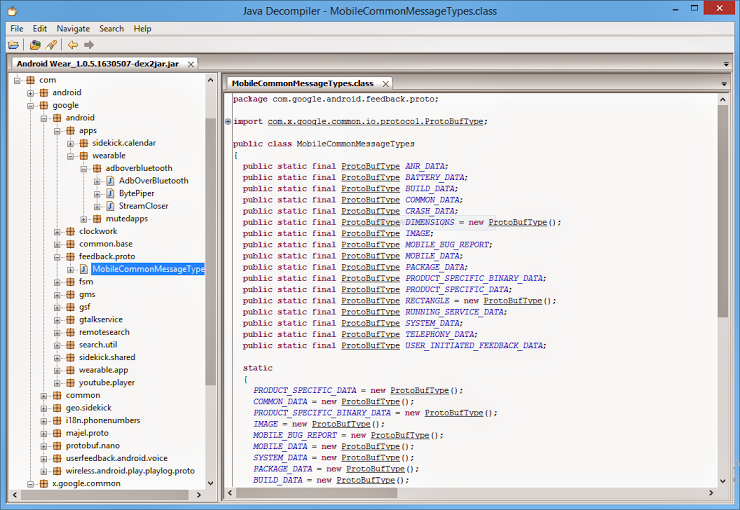
Java decompiler is used to decompile and analyse byte codes. It’s a GUI based utility to view .class files. You just need to load jar file, to view .class files of project.
Apktool
Download Apktool
Using Dex2Jar, you can get and play source code files, but to play with resource files, we require Apktool. Using Apktool, we can decode resource into nearly original form and rebuild them after making some modifications.
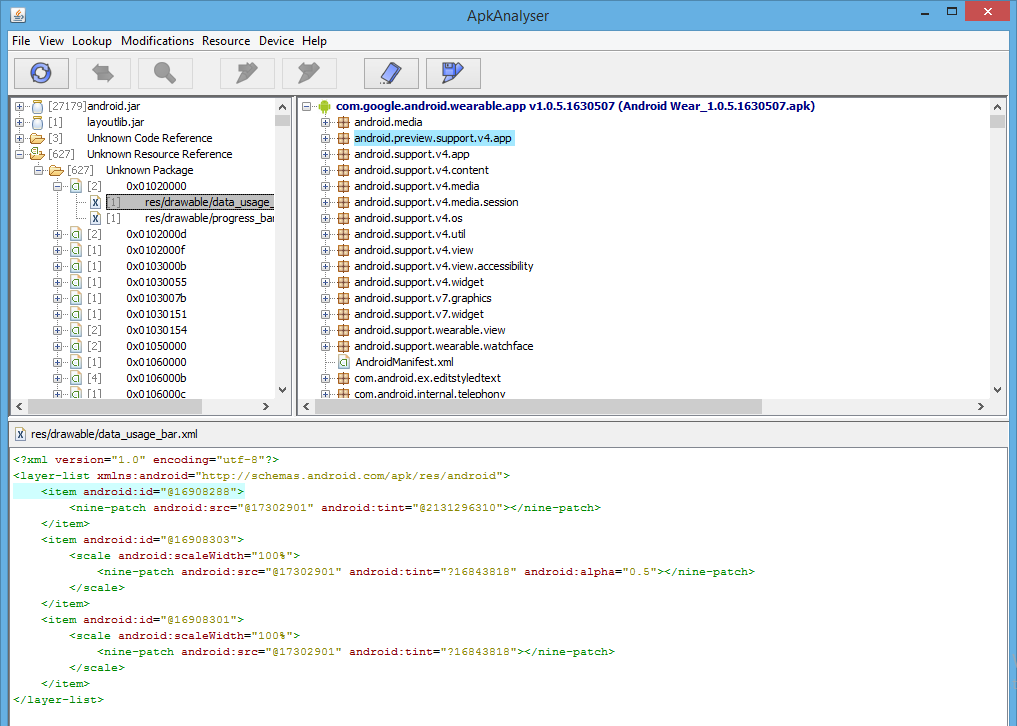
Apk Analyser
Apk analyser is a tool provided by sony mobile. They call it as an app analysis tool. Yoou can use to analyse API references, view application architecture and dependencies, and disassemble bytecodes in Android apps. It provides a good looking UI for your application architecture and dependencies.
You can use Apk Analyser tool if you don’t want to perform lengthier process using above tools.
[alert style=”green”] Note: Before starting reverse engineering of particular applications, keep “proguard” in mind because you won’t be able to perform 100% reverse engineering if proguard is enabled by application developer. I mean if application developer has worked hard for obfuscating code then it would not be easier. [/alert]Using Dex2jar, JD-GUI and Apktool
Personally I use these tools and practice to reverse engineer any android applications. If you haven’t downloaded yet, then please go ahead and download it.
Steps:
- Create a directory with name “RE-Android”
- Keep all the tools (Dex2jar, apktool, jd-gui) into this directory
- Extract dex2jar and jd-gui zip files into the same directory.
- Now get an apk of particular application, to get that you will require ES file manager or any application which allows to export apk. For the demo purpose, I have downloaded Android wear application.
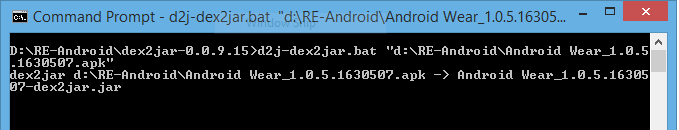
- Execute the below command to convert the apk file into jar. Once it gets converted successfully, it will create a jar file with the name “Android Wear_1.0.5.1630507-dex2jar” for the “Android Wear_1.0.5.1630507.apk”.
D:\RE-Android\dex2jar-0.0.9.15>d2j-dex2jar.bat "d:\RE-Android\Android Wear_1.0.5 .1630507.apk"
- Now start jd-gui application and open the “Android Wear_1.0.5.1630507-dex2jar” file and enjoy reading other application’s classes and code.
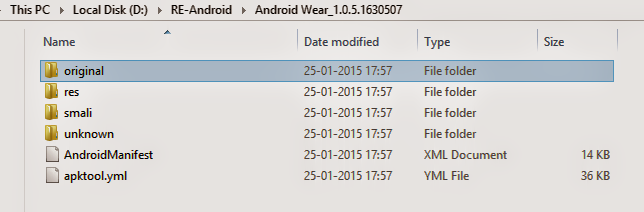
- Execute apktool d yourapk.apk command to decode resources. Executing this command will give you below project structure.
D:\RE-Android>apktool_2.0.0rc3.jar d "Android Wear_1.0.5.1630507.apk"
As I mentioned earlier, Dex2jar only decompiles classes and code. To decode resources, we have to use Apktool.
Using Apk analyser
If you don’t want to perform all the above steps and want to view decompiled apk structure into the GUI then APK analyser can be of help, but it gives assembly like code. It would be hard for you if you haven’t worked or deal with assembly code yet.
Steps:
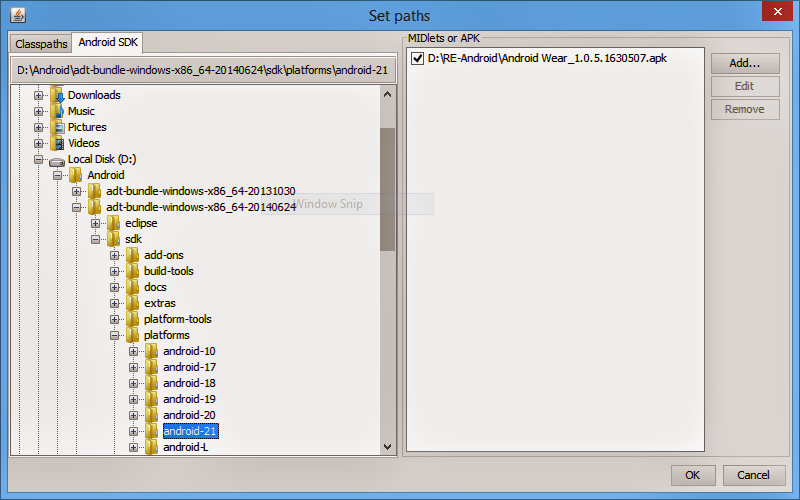
- Open Apk analyser application
- Set required paths like android sdk and apk file location.
- Start analysing the application by selecting File => Analyse. It would take time to dissemble the apk.
In Summary
This bring us to the end of this part. In this episode, we talked about reverse engineering, which is a process to extract knowledge or useful information from any product, whether it’s applied while rebuilding a bike or a car or any human made product. You would come to learn many new and interesting stuffs after breaking down the actual product into the different parts and putting them together again.
I hope to explore more about reverse engineering in future. I hope you liked this part of lazy android developer series. Till the next part, keep reverse engineering applications, keep extracting resources/code and keep learning from it.